How to configure passwordless login in macOS and Linux

Once you set up a shell user and try to log in via SSH, you’ll find you must enter your password each time. If you’d like to avoid entering your password every time, you can set up Passwordless Login. This way, you’ll be able to automatically login each time immediately without needing to enter your password.
Anas Alshanti©
Saturday 19 February 2022 : Added “How to enable or disable public key authentication in SSH” section
- STEP 1 – Generating the key pair
- STEP 2 – Copying the public key to server
- STEP 3 – Test the connection
- How to enable or disable public key authentication in SSH
STEP 1 – Generating the key pair
On your home computer
Generate an ed25519 and ecdsa private key using ssh-keygen
If you’re using Linux or Mac OS X, open your terminal and run the following command under your username:
ssh-keygen -t ed25519 -f ~/.ssh/id_ed25519
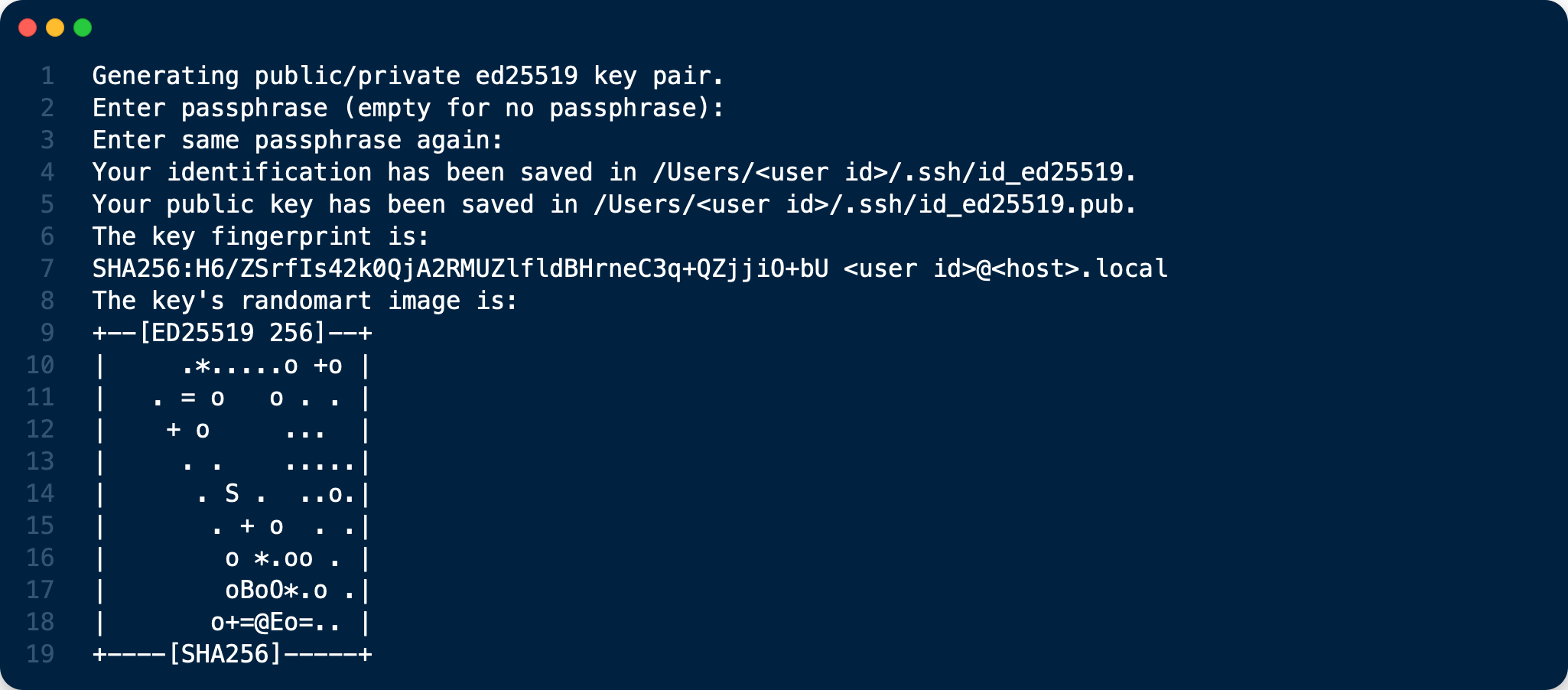
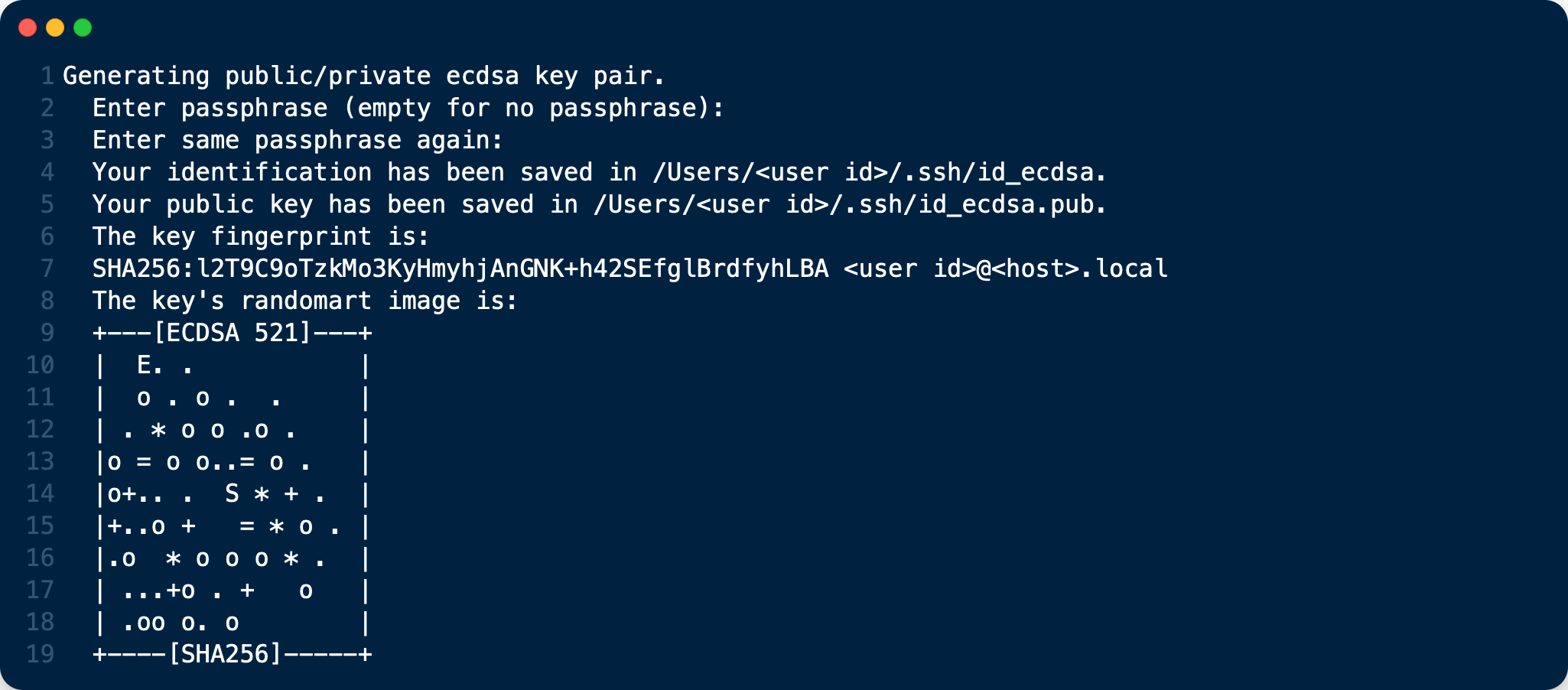
ssh-keygen -t ecdsa -b 521 -f ~/.ssh/id_ecdsa
The minimum key size shall be 512 bits for ECDSA.
- You do not need to enter a passphrase, but it’s highly recommended as it protects your private key if compromised. If so, someone would still need your passphrase in order to unlock it. The exception to this is if you’re running an automated process such as as cron job. You should then leave the password out. From ssh.com: “Generally all keys used for interactive access should have a passphrase. Keys without a passphrase are useful for fully automated processes.”
- ED25519 keys should be favoured over ECDSA keys when supported by SSH clients and servers. The Ed25519 algorithm, which is considered state of the art. Elliptic curve algorithms in general are sleek and efficient and unlike the other well known elliptic curve algorithm ECDSA.
STEP 2 – Copying the public key to server
Run the following command to copy the public key on your local computer to server.
cat ~/.ssh/id_ed25519.pub | ssh <username>@<server.domain-name.io> "mkdir -p ~/.ssh; cat >> ~/.ssh/authorized_keys"
The commands above create a new folder /.ssh with 700 permissions. In that folder is your authorized_keys file which was just copied from your home computer which has 600 permissions.
STEP 3 – Test the connection
ssh <user_id>@<server_name>
The login connection must be passwordless now !
How to enable or disable public key authentication in SSH
SSH server in most systems is by default configured to allow public-key authentication. The method will enable you to use your public and private key pair to log in to an SSH server without using a username and password.
Public key authentication method for SSH could be enabled or disabled by configuring the PubkeyAuthentication directive in the sshd_config file on the server.
Steps to enable or disable public key authentication in SSH:
1. Launch your preferred terminal application.
2. Open /etc/ssh/sshd_config configuration file
sudo vi /etc/ssh/sshd_config
3. Search for PubkeyAuthentication and set the option to yes or no.
PubkeyAuthentication yes
Add the line if it doesn’t already exist and remove # at the beginning of the line if it exists. Set it to yes to allow public key authentication method and no to disallow.
Make sure your other authentication method such as password is enabled before disabling public key authentication method as you might completely lose remote access to your server.
4. Reload or restart SSH server service.
sudo systemctl restart sshd