How to host a site on the Dark Web

In this tutorial we will be setting up a server that will host a static site on the Dark Web. We will be using Tor Hidden services for this. We will be using static files for simplicity and security.
- Tor
- Nginx
- nginx.conf
- Web Server Root Directory
- Remove Nginx Default
- Add Available Site
- Tor Browser
- Conclusion
This tutorial is intended for and tested on a remote server running Debian. This server should be properly secured for production use. If you need assistance setting up a server, please read my post Hardening Linux Server Setup - Hardening SSH Server Setup and Hardening Web Server Setup. This tutorial also will assume that you have a basic familiarity with the Dark Web and you already have the Tor Browser.
Tor
The Tor packages found in the default repositories for Ubuntu or Debian are not reliably updated. The Tor project maintains their own repository. We must add that repository.
sources.list: You’ll need to set up our package repository before you can fetch Tor. First, you need to figure out the name of your distribution. A quick command to run is lsb_release -c or cat /etc/debian_version. If in doubt about your Debian version, check the Debian website. For Ubuntu, ask Wikipedia.
You need to add the following entries to /etc/apt/sources.list or a new file in /etc/apt/sources.list.d/:
sudo vi /etc/apt/sources.list
Add the following to the end of the file
deb https://deb.torproject.org/torproject.org stretch main
deb-src https://deb.torproject.org/torproject.org stretch main
Then add the gpg key used to sign the packages by running the following commands at your command prompt:
gpg --keyserver keys.gnupg.net --recv A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89
root@n0d3:~# gpg --keyserver keys.gnupg.net --recv A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89
gpg: keybox '/root/.gnupg/pubring.kbx' created
gpg: /root/.gnupg/trustdb.gpg: trustdb created
gpg: key EE8CBC9E886DDD89: public key "deb.torproject.org archive signing key" imported
gpg: Total number processed: 1
gpg: imported: 1
gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
Run the update.
sudo apt-get update
Then install Tor
sudo apt-get install tor deb.torproject.org-keyring
If after do the last command you get this : tor : Depends: libevent-2.0-5 (>= 2.0.10-stable) but it is not installable. So fix it manually : wget http://ftp.de.debian.org/debian/pool/main/libe/libevent/libevent-2.0-5_2.0.21-stable-3_arm64.deb ; apt install ./libevent-2.0-5_2.0.21-stable-3_arm64.deb ; rm ./libevent-2.0-5_2.0.21-stable-3_arm64.deb
The Hidden Service
We need to edit the Tor configuration file to enable our hidden service. First we will make a backup of this configuration file.
sudo cp /etc/tor/torrc /etc/tor/OLD.torrc
Then edit the configuration file.
sudo vi /etc/tor/torrc
By default all Tor client services, relays, and hidden services are commented out and disabled. Let’s active the hidden service. Find the section for hidden services. It will look something like this.
############### This section is just for location-hidden services ###
## Once you have configured a hidden service, you can look at the
## contents of the file ".../hidden_service/hostname" for the address
## to tell people.
##
## HiddenServicePort x y:z says to redirect requests on port x to the
## address y:z.
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80
#HiddenServiceDir /var/lib/tor/other_hidden_service/
#HiddenServicePort 80 127.0.0.1:80
#HiddenServicePort 22 127.0.0.1:22
Uncomment the following lines.
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80
The hidden services section should now look like this.
############### This section is just for location-hidden services ###
## Once you have configured a hidden service, you can look at the
## contents of the file ".../hidden_service/hostname" for the address
## to tell people.
##
## HiddenServicePort x y:z says to redirect requests on port x to the
## address y:z.
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
#HiddenServiceDir /var/lib/tor/other_hidden_service/
#HiddenServicePort 80 127.0.0.1:80
#HiddenServicePort 22 127.0.0.1:2
Restart Tor
sudo service tor restart
And check the Tor status
sudo systemctl status tor
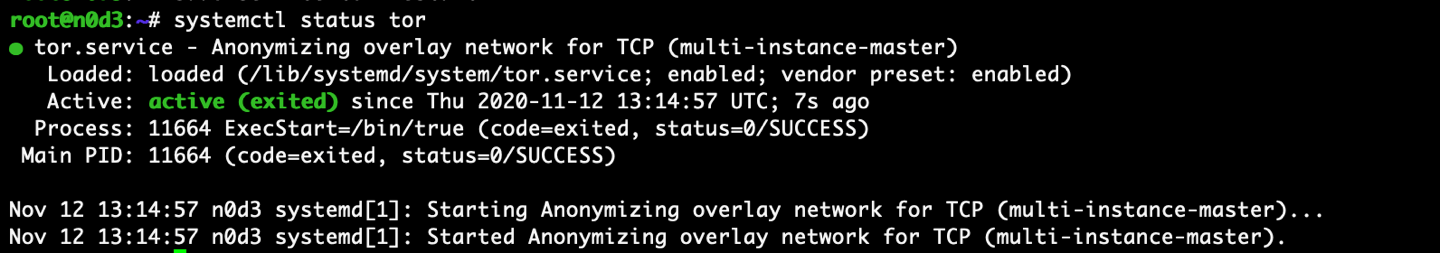
Couple of files should have generated by Tor. First is a hostname file. Open it up to get your .onion address.
sudo cat /var/lib/tor/hidden_service/hostname
My file contained 6ad4242dqvoc7e7jgh5laivs2fs7l4u2ej2gscaxtc5wbxlskow4vqd.onion. Your file should contain something similar. The other file is a private and public key. Open it up and take a look.
sudo ls -lrt /var/lib/tor/hidden_service/
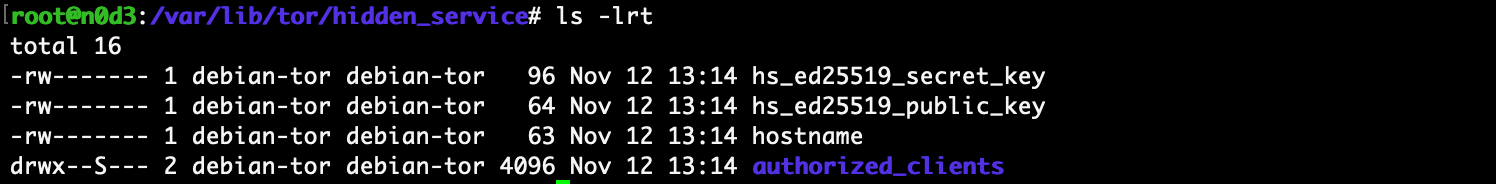
With these files two files you can move your server to a new machine if eventually necessary. Copy these file and keep them secure.
Nginx
nginx is a good web server for this project. Install Nginx.
sudo apt-get install nginx
Your server should be running a firewall. I recommend the Uncomplicated Firewall (UFW). If you need help with UFW, check out, A Guide to the Uncomplicated Firewall (UFW) for Linux. The following command will allow HTTP traffic.
sudo ufw allow 'Nginx HTTP'
Visit your server’s IP address to verify that the web server is operational.
If things are working correctly, remove this rule. Then reload the firewall.
sudo ufw deny 'Nginx HTTP'
sudo ufw reload
nginx.conf
Edit the main Nginx configuration file to disable undesirable information sharing.
sudo vi /etc/nginx/nginx.conf
Inside the http block add the following
server_name_in_redirect off;
server_tokens off;
port_in_redirect off;
Then restart the Nginx server.
sudo systemctl restart nginx
Web Server Root Directory
Make a directory to hold our files for the web server.
sudo mkdir /var/www/dark_web
Make and edit an index.html file for your site.
sudo vi /var/www/dark_web/index.html
Inside just put anything. We don’t need actual html, just something kinda unique for right now.
Welcome to my dark web page
Set the permissions so that Nginx can access the files.
sudo chmod 755 /var/www/dark_web
Remove Nginx Default
Remove the default site.
sudo rm /etc/nginx/sites-enabled/default
sudo rm /etc/nginx/sites-available/default
Add Available Site
Make a new site in the sites-available directory.
sudo vi /etc/nginx/sites-available/dark_web
Inside add the following replacing the root and server_name values for your instance.
server {
listen 127.0.0.1:80;
root /var/www/dark_web/;
index index.html;
server_name 6ad4242dqvoc7e7jgh5laivs2fs7l4u2ej2gscaxtc5wbxlskow4vqd.onion;
}
Add this site the the site_enabled.
sudo ln -s /etc/nginx/sites-available/dark_web /etc/nginx/sites-enabled/
Then restart the Nginx server.
sudo systemctl restart nginx
Tor Browser
Open up your Tor Browser (you can download it here) and visit your .onion address that was generated earlier. If the system is properly operational then you will see the dummy index.html page that we made previously.
Conclusion
So now you have a site on the Dark Web. Any files in the /var/www/dark_web will be available online. If you use a static site generator this would be the folder to output to.